By Peter Kardel
IT people tend to be control freaks. That’s good. You want that locked-down, buttoned up, backups covered, everything triple-checked when it comes to your business IT. Your amazing customer service depends on it, your reputation is protected by it. So there’s no doubt a sense of urgency burns in the heart of your IT guy when it comes to your business data security. As we’ve discussed in previous posts, the threats are growing in frequency, sophistication and in profitability for the bad guys. With the sinister evolution into crypto-ransom attacks, hackers simply lock you out of your data, making you pay to get it back. Business owners can take solace in the sentiment that “nobody is interested in our data, so we’re safe.” To which the hacker replies “yeah, but you are!” [insert sinister laugh]
It is no wonder then that your IT guy has got worries . . . and lots of tools, policies and “best practices” to keep you safe. These “shiny boxes” are the technical armor plating that every business needs. But we all know every set of armor has its ‘chinks.’ And oh, does your security armor have a weakness. A huge, squishy one that is always on the move and ever changing. Your biggest security weaknesses are your people.
Using research-based, social engineering approaches, hackers have learned to get inside the heads of your people . . . getting them to throw doors wide open to the data inner sanctum at the heart of your business. The very tools we rely on to reach our customers, future employees and business prospects are being exploited to trick your people. Think of the hiring manager posting on LinkedIN, later getting an email from a perfect looking job candidate . . . they are expecting, even looking for it and are inherently vulnerable to clicking something they shouldn’t. If your people are unwittingly aiding and abetting the attacker, no amount of IT security is going to keep the bad guys out. Our people are letting in through the front door while IT is busy checking the windows and guarding the back door. Your IT team might be on a war footing, but your employees are acting life civilians, thinking that the fighting is “over there.” This reminds me of the powerful WW II era posters reminding citizens that any sensitive snippet of information they share could end up in the hands of the enemy. A causal comment at the grocery store about a brother shipping out tonight on a Liberty Ship could alert the German Wolfpacks to be on the hunt for an allied supply convoy. People died when intel like this was  snapped up by the German espionage working inside the US during the war. This “fifth column” was innocuous, camouflaged and ubiquitous during the war. So it is with the agents operating in the cyberwar. In this war, the fight is over your money and reputation. It is time your people join the fight! It is time to put your staff through cyber security boot camp.
snapped up by the German espionage working inside the US during the war. This “fifth column” was innocuous, camouflaged and ubiquitous during the war. So it is with the agents operating in the cyberwar. In this war, the fight is over your money and reputation. It is time your people join the fight! It is time to put your staff through cyber security boot camp.
Here’s what it should look like. Start with an assessment to measure where the gaps in ‘phishing’ awareness lie in your team, then assign training tailored to the needs across your team, then retest. Along the way, send out fun to read articles around IT security. We have selected KnowBe4 (https://www.knowbe4.com/) for this. The training is terrific. They have created the right blend of techie vs savvy with videos featuring legendary hacker gone good, Kevin Mitnick. Some similar training is too polished and light on the details. Their message is simply, “hackers are out there and can get you if you’re not careful.” The Mitnick videos are more impactful because they show at a high level how the attacks are carried out, making the lessons far more visual and the message more sticky. The administration of the testing and education campaigns are very simple to manage in their portal. You can track over time the improvement to your teams IT security chops. This is very important not only for measuring ROI, but this is also a requirement in every IT Security Policy framework in every industry. Simply put, you are required by law or fiduciary responsibility to have an adequate IT Security Policy in place, and a critical part of that is regular, documented end-user IT security training. This requirement is articulated in the SANS Security CIS Critical Security Controls – Version 6.0, Section CSC 17.
Don’t get caught without security controls in place; you are obligated legally and professionally. A report released by California Attorney General Kamala Harris makes it clear: the CIS 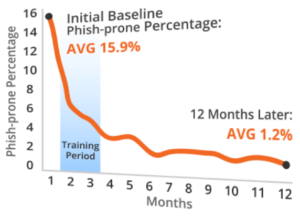 Critical Security Controls represent “a minimum level of information security that all organizations that collect or maintain personal information should meet.” Further, the report concludes that failing to implement the Controls “constitutes a lack of reasonable security.” You of course want to prevent a damaging breach, but if one does occur, woe to the organization that has not taken some simple steps to meet these IT security requirements. We have secured volume pricing for the KnowBe4 training through our trade association, so we can provide it to our clients at a very reasonable cost. So, if you’re IT guy is looking more disheveled than usual, it might be because he was tossing and turning all night, haunted by nightmares of a cyber-attack bringing down your business. Give him a break, take this simple step to protect your business and your customers’ data. Implement IT security awareness training in your business today!
Critical Security Controls represent “a minimum level of information security that all organizations that collect or maintain personal information should meet.” Further, the report concludes that failing to implement the Controls “constitutes a lack of reasonable security.” You of course want to prevent a damaging breach, but if one does occur, woe to the organization that has not taken some simple steps to meet these IT security requirements. We have secured volume pricing for the KnowBe4 training through our trade association, so we can provide it to our clients at a very reasonable cost. So, if you’re IT guy is looking more disheveled than usual, it might be because he was tossing and turning all night, haunted by nightmares of a cyber-attack bringing down your business. Give him a break, take this simple step to protect your business and your customers’ data. Implement IT security awareness training in your business today!
Need help with your Business IT?
Let’s talk. If we’re not the best fit, we’ll refer you to someone who is: Contact Us.
